1

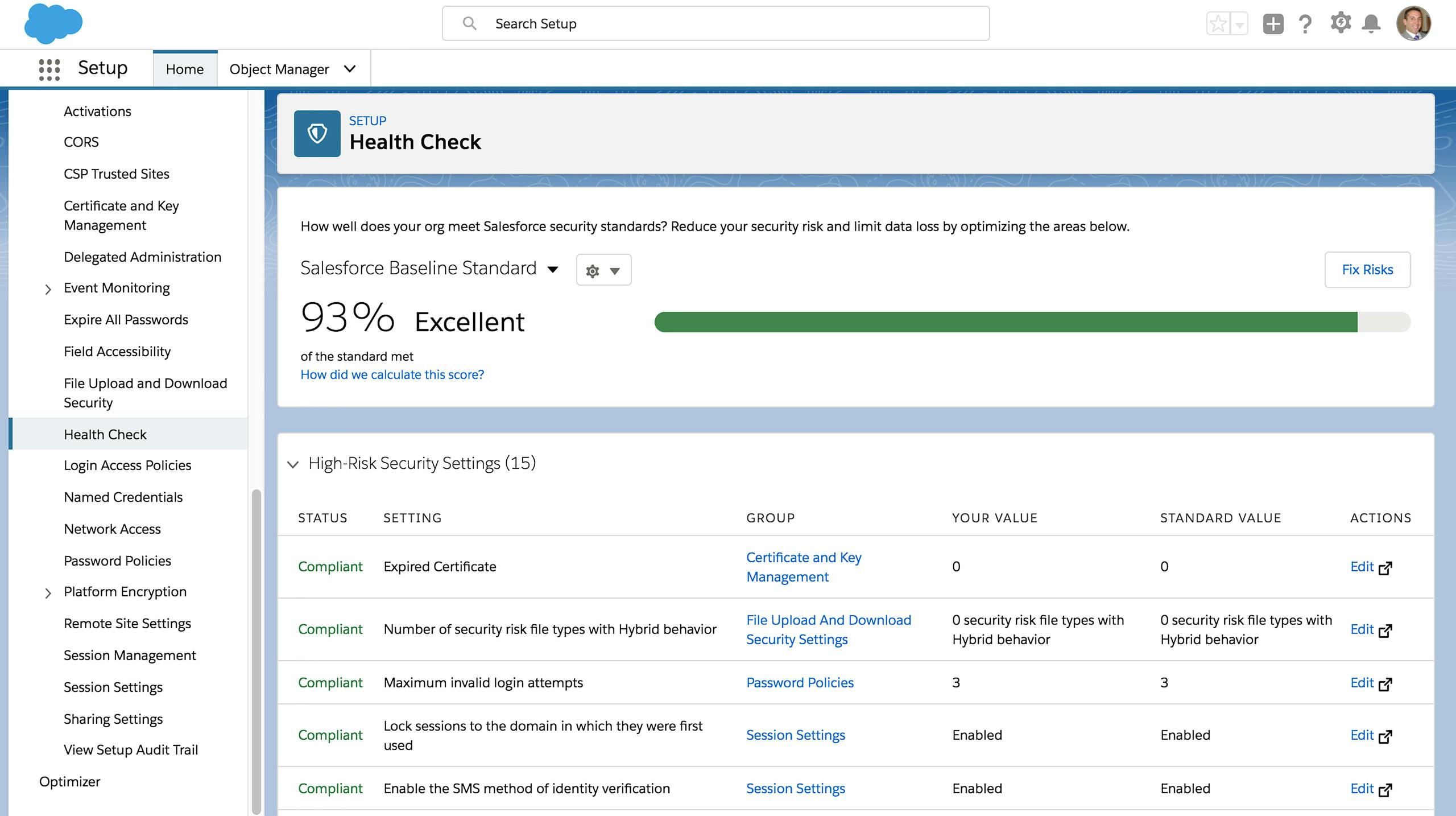
Set security baselines
Compare your current security settings to an established baseline. Admins can spot High, Medium, and Low-Risk setting impacting security scores, setup a custom security baseline as well as fix all of the risks with just a few clicks.


Background
Salesforce Shield consists of 3 key services - Platform Encryption, Event Monitoring, and Field Audit Trail - to protect, monitor, and retain critical Salesforce data.

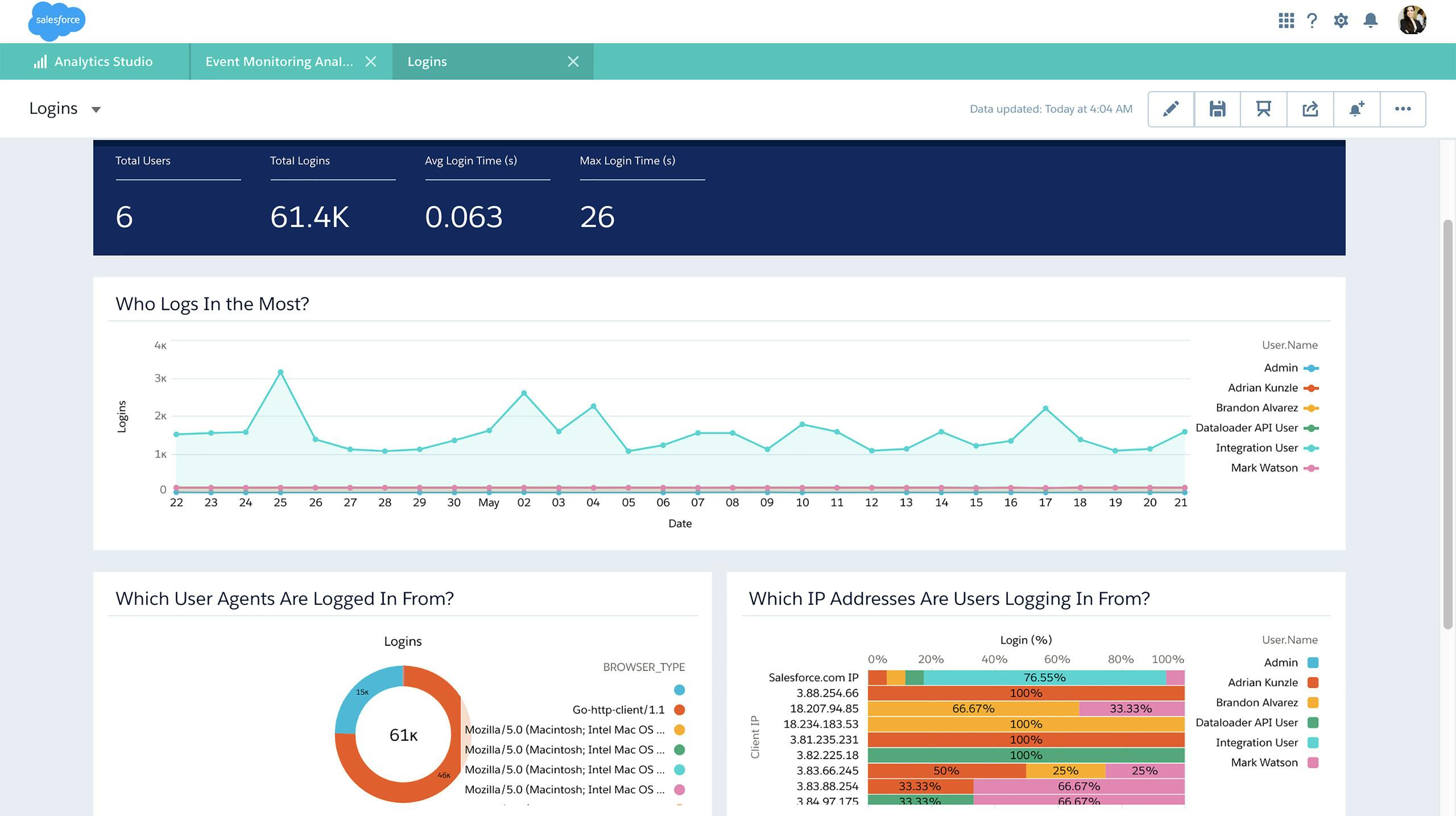
Monitor Events
Event Monitoring lets you see the granular details of user activity in your organization. Salesforce offers the Event Monitoring Analytics App within Einstein Analytics to visually analyze event data from a security, user adoption, or performance optimization perspective. This login dashboard shows which users are most active in the system, where they’re logging in from, and which agents are being used to access Salesforce.

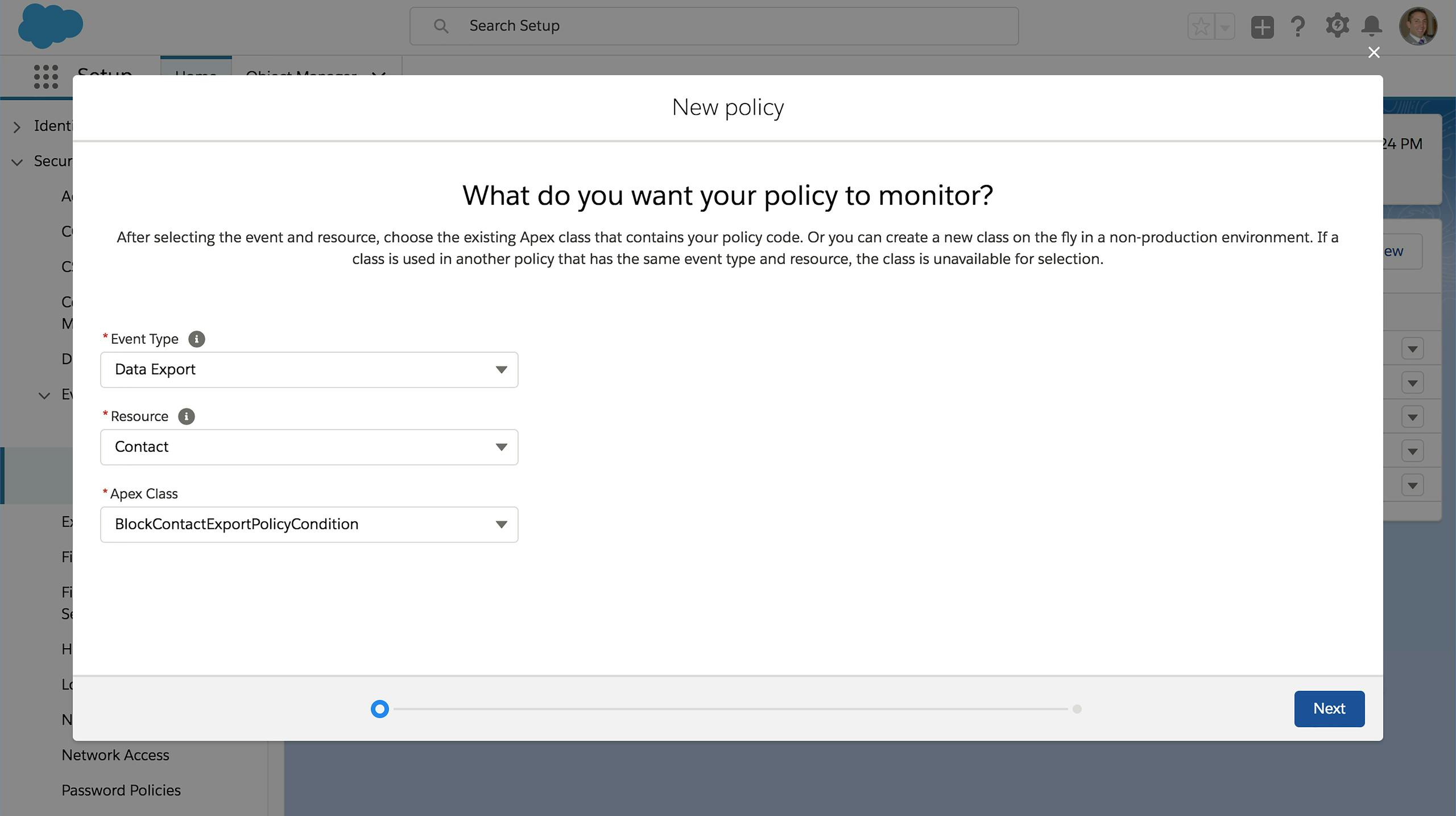
Secure Transactions
Create event-driven policies to proactively monitor Salesforce in real-time. Take specific actions when those policies are triggered. You can; block an attempted operation, require step-up two-factor authentication, or end a user session.

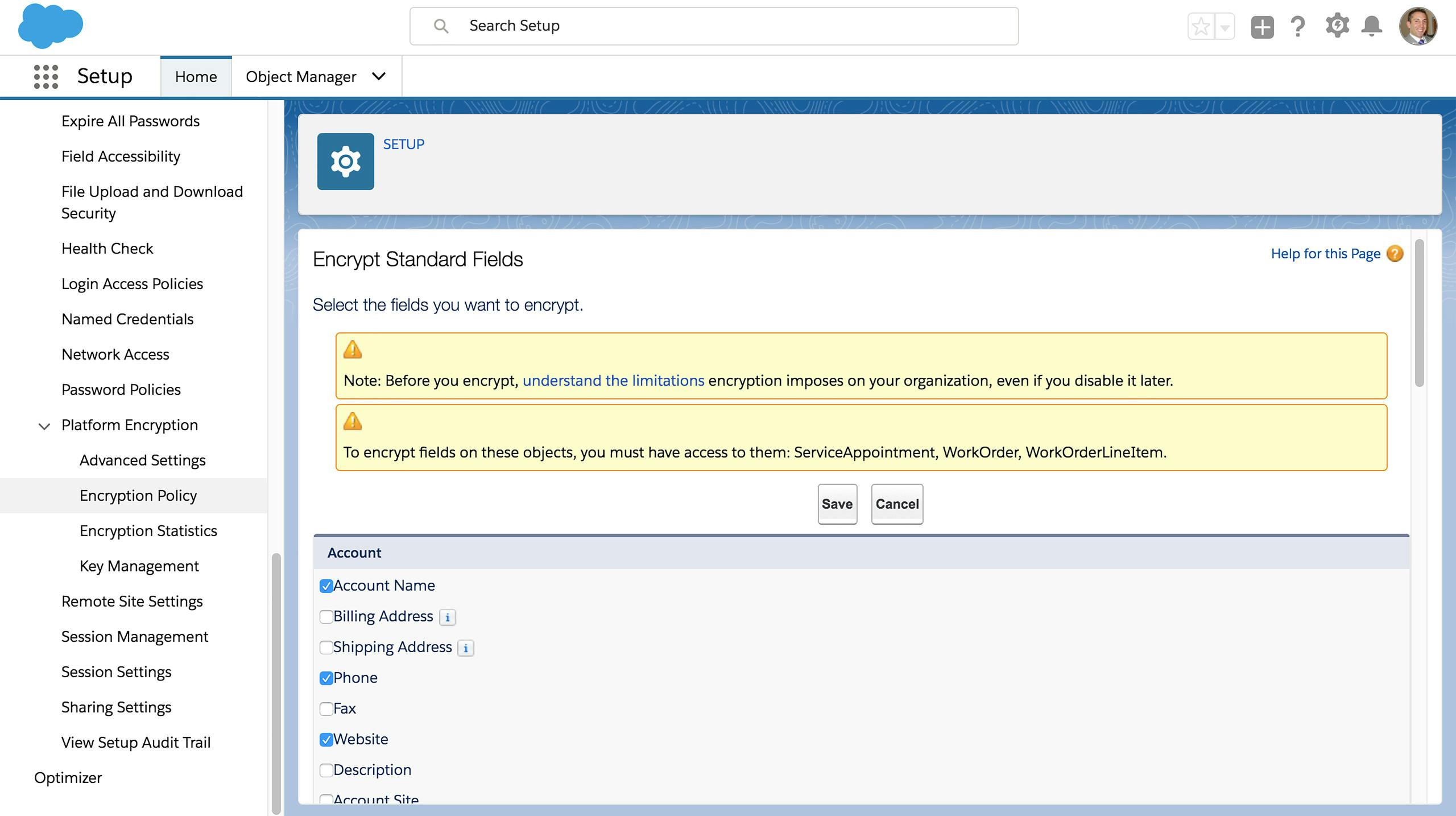
Encrypt your Data
Apply strong encryption to sensitive data at rest, including standard fields, custom fields, files, and attachments. Encryption policies can be easily set in the user interface with just a few clicks.

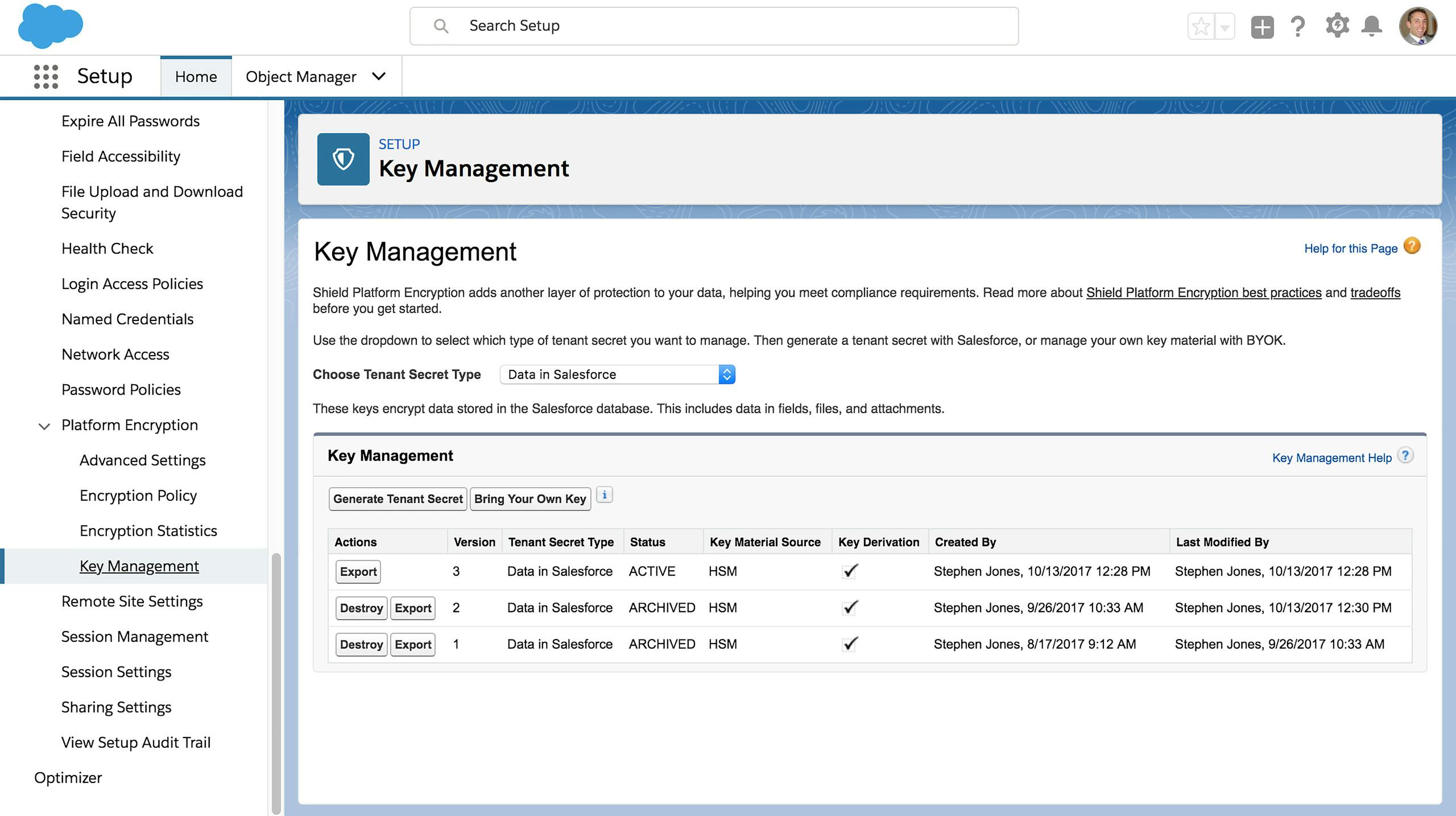
Manage Keys and Secrets
Allows full control over the encryption key lifecycle, including generating, exporting, importing, and destroying tenant secrets. With Salesforce’s Bring Your Own Key capability, administrators can upload a tenant secret or an encryption key generated outside of Salesforce.

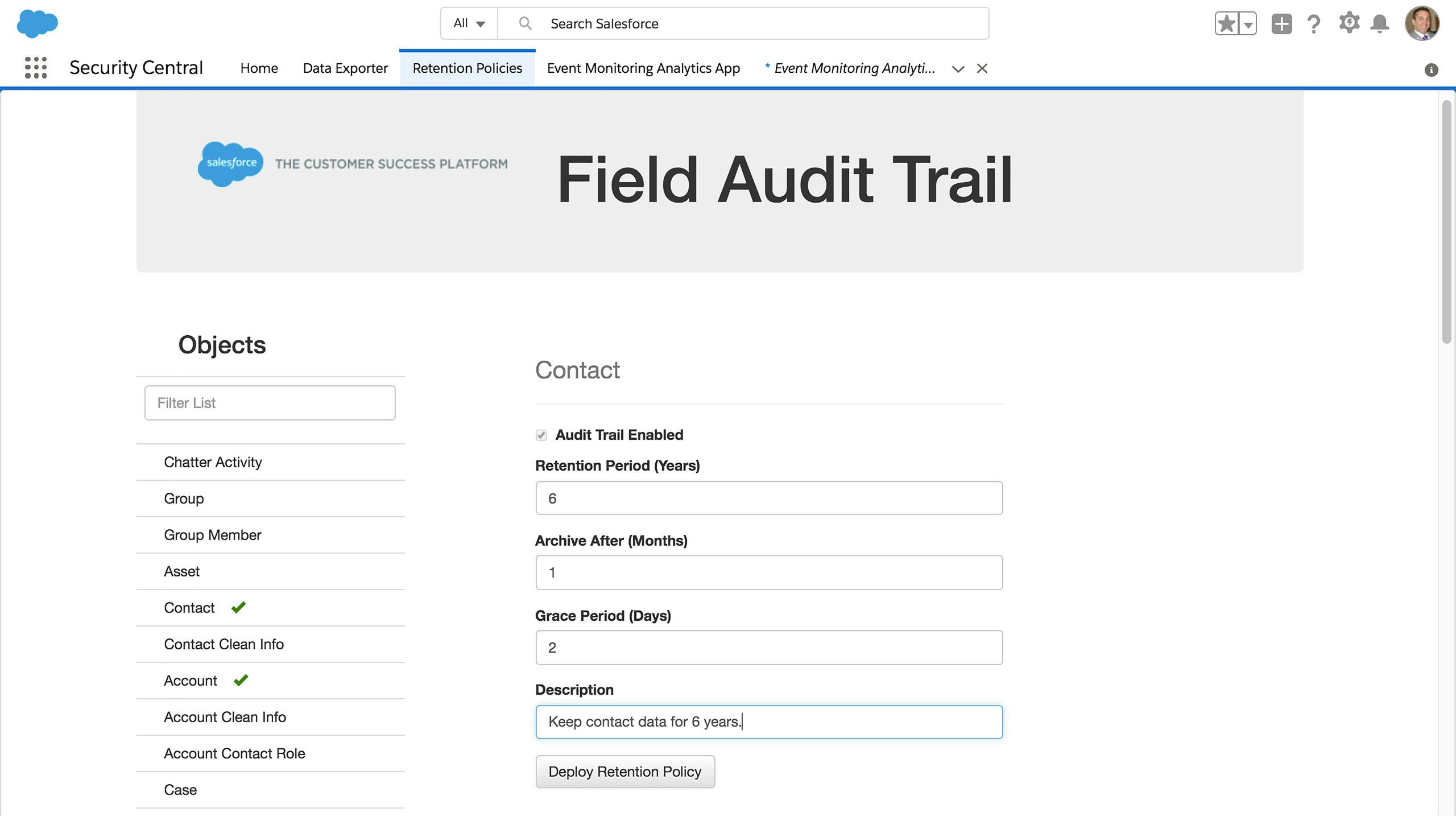
Review the Audit Trail
Meet strict data auditing and retention regulations by creating object-level policies to retain archived field history data for up to ten years. Use the Salesforce Metadata API, develop a custom page (seen here), or use a 3rd party application to create and maintain policies.

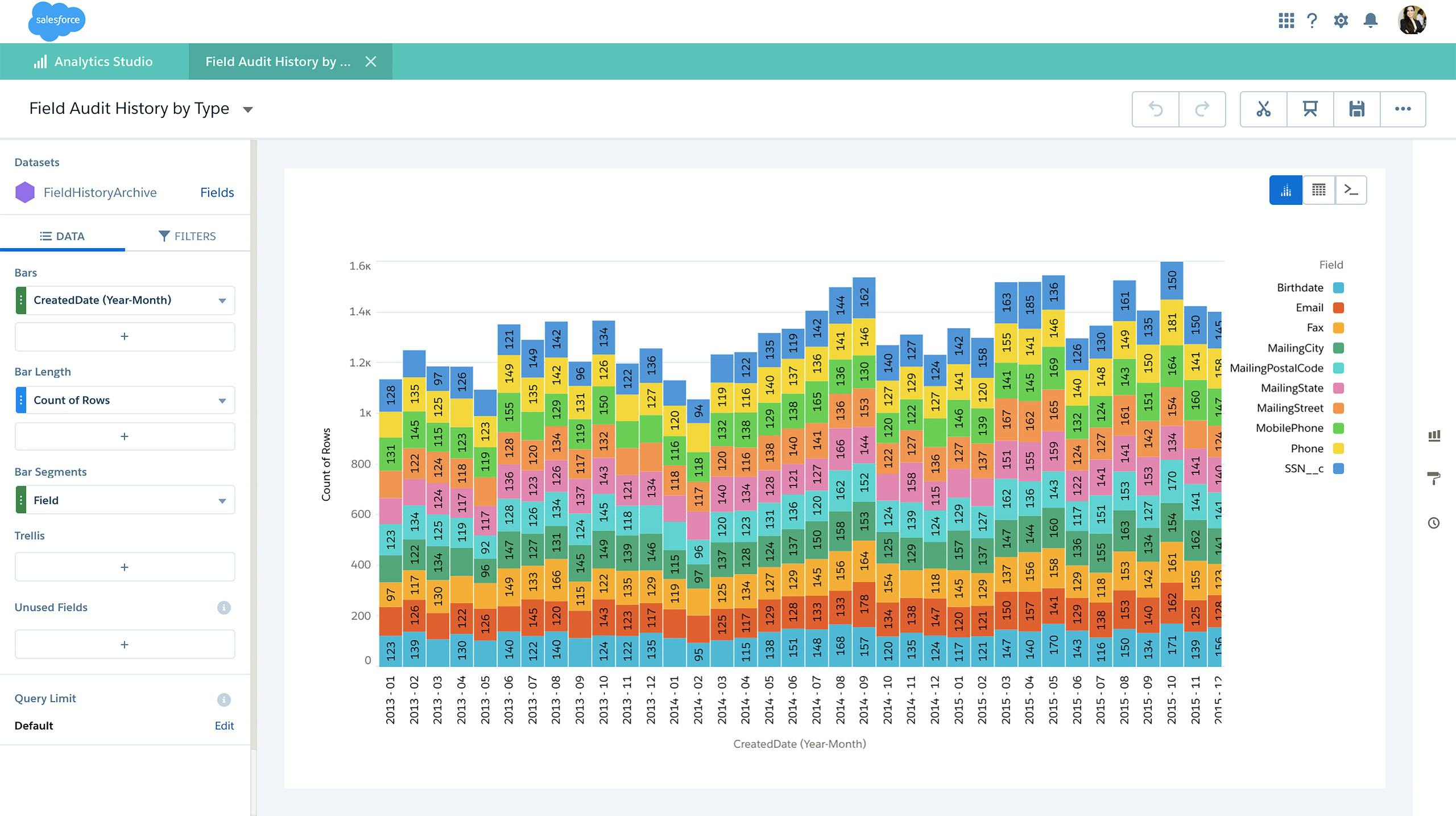
Ensure Accuracy
Ensure your data is accurate, complete and reliable by looking at who, what, and when your data changes in easy to read dashboards and charts.


Set security baselines
Compare your current security settings to an established baseline. Admins can spot High, Medium, and Low-Risk setting impacting security scores, setup a custom security baseline as well as fix all of the risks with just a few clicks.


Background
Salesforce Shield consists of 3 key services - Platform Encryption, Event Monitoring, and Field Audit Trail - to protect, monitor, and retain critical Salesforce data.


Monitor Events
Event Monitoring lets you see the granular details of user activity in your organization. Salesforce offers the Event Monitoring Analytics App within Einstein Analytics to visually analyze event data from a security, user adoption, or performance optimization perspective. This login dashboard shows which users are most active in the system, where they’re logging in from, and which agents are being used to access Salesforce.


Secure Transactions
Create event-driven policies to proactively monitor Salesforce in real-time. Take specific actions when those policies are triggered. You can; block an attempted operation, require step-up two-factor authentication, or end a user session.


Encrypt your Data
Apply strong encryption to sensitive data at rest, including standard fields, custom fields, files, and attachments. Encryption policies can be easily set in the user interface with just a few clicks.


Manage Keys and Secrets
Allows full control over the encryption key lifecycle, including generating, exporting, importing, and destroying tenant secrets. With Salesforce’s Bring Your Own Key capability, administrators can upload a tenant secret or an encryption key generated outside of Salesforce.


Review the Audit Trail
Meet strict data auditing and retention regulations by creating object-level policies to retain archived field history data for up to ten years. Use the Salesforce Metadata API, develop a custom page (seen here), or use a 3rd party application to create and maintain policies.


Ensure Accuracy
Ensure your data is accurate, complete and reliable by looking at who, what, and when your data changes in easy to read dashboards and charts.


Set security baselines
Compare your current security settings to an established baseline. Admins can spot High, Medium, and Low-Risk setting impacting security scores, setup a custom security baseline as well as fix all of the risks with just a few clicks.






